c2_with_ad_dc
The c2_with_ad_dc playbook can be used to set up the components needed to test a network security stack's ability to prevent/detect a myriad of different command and control tunnels, Windows domain reconnaissance techniques and data exfiltration from a Windows domain. The playbook creates a temporary Active Directory Domain Controller that can be used to perform reconnaissance against and copy/exfiltrate data from without impacting your real, production Active Directory domain. The playbook also establishes a command and control tunnel with a cloud based PowerShell Empire container task.
Requirements
Running this playbook requires the following pre-existing components:
- A remote Trainman container task running in the monitored network to run the Active Director Domain Controller.
- A remote Trainman container task running in the monitored network to establish a C2 tunnel with an external PowerShell Empire container task.
Note that the two remote Trainman container tasks should be running on separate physical hosts if you expect your network monitoring capabilities to observe traffic between the two containers.
Architecture
The architecture and workflow of this playbook looks as follows:
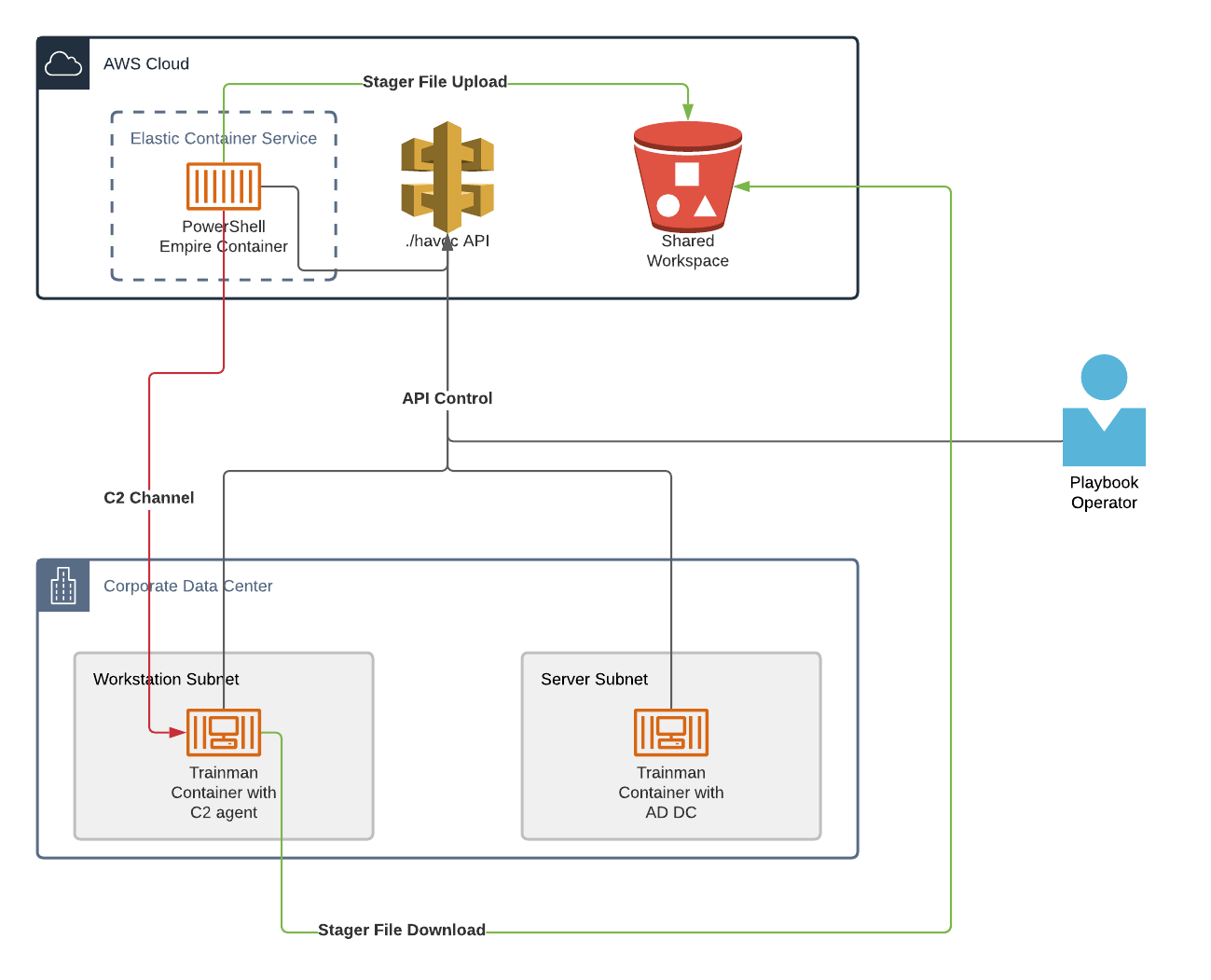
Configuration
To configure this playbook, use the ./havoc -c CLI option, select the number associated with the c2_with_ad_dc playbook and provide the requested details:
$ ./havoc -c
1) c2_and_http_server 7) pse_recon_portscan
2) c2_with_ad_dc 8) pse_recon_reverse_dns
3) cve_2021_44228_exploit_and_c2 9) pse_recon_share_finder
4) cve_2021_44228_testing 10) simple_exfil
5) pse_lateral_movement_invoke_wmi 11) windows_exfil
6) pse_recon_bloodhound 12) windows_recon
Select a playbook to install: 2
Configuring playbook c2_with_ad_dc.
If you have previously configured this playbook, configuring it again will delete the existing configuration.
Are you sure you want to continue? [Y/N]: y
Creating a customized c2_with_ad_dc.ini file.
Provide a value for each parameter.
Press enter without providing a value to accept the default.
[c2_task]
listener_type [http_malleable]: <listener_type>
listener_profile [sofacy]: <listener_profile>
listener_port [80]: <listener_port>
listener_tls [no]: <yes|no>
domain_name [None]: <domain_name|None>
cert_subj [/C=US/ST=Utah/L=Lehi/O=Your Company, Inc./OU=IT/CN=$HOST]: <cert_subj>
[remote_ad_task]
task_name [remote_trainman_ad]: <remote_trainman_ad_task_name>
ad_tld [local]: <top_level_domain_of_ad>
ad_domain [samdom]: <ad_domain>
ad_realm [SAMDOM.LOCAL]: <ad_realm>
user_name [jdisco]: <user_name>
user_password [user_password_152637]: <user_password>
admin_password [samdom_password_152637]: <admin_password>
[remote_c2_agent_task]
task_name [remote_trainman_agent]: <remote_trainman_agent_task_name>
<snip - installing required Python modules>
Playbook c2_with_ad_dc configured.
$
Execution
To execute this playbook, run the following ./havoc CLI command (where is replaced with the ./havoc config profile name that you would like to authenticate to the ./havoc API with):
$ ./havoc -e c2_with_ad_dc <profile>
Clean up
Error handling
If the playbook encounters errors during execution, it should automatically switch to a clean_up function and delete any resources that it created. If the playbook is hung on a specific task, you can press Ctrl+C to terminate the playbook and initiate the clean_up function.
Successful execution
After the playbook executes all operations successfully it will pause itself and leave all corresponding resources in place so that you can utilize its components with other playbooks such as the windows_recon playbook. When you're finished running the desired activities with the components from this playbook, pressing the "enter" key at the paused prompt will initiate the playbook's clean_up function.
Associated resources
This playbook creates and destroys the following resources:
- A PowerShell Empire cloud container task
- A PowerShell Empire Listener
- A PowerShell Empire Stager file that gets saved to the local directory where ./havoc CLI was executed from
- The file name will reflect the C2 Listener profile or Listener type if no Listener profile is used.
- A portgroup that restricts inbound access to the PowerShell Empire's Listener port to just the public IP address of the remote_c2_agent_task.
- A shared Workspace file that is a copy of the PowerShell Empire Stager file.
- The file name will reflect the C2 Listener profile or Listener type if no Listener profile is used.
If you're uncertain whether the clean_up function completed successfully, the following ./havoc CLI console commands can be used to check which resources are still present:
list_tasks
list_portgroups
list_files
Updated over 2 years ago
