cve_2021_44228_testing
This playbook was developed to identify the specific versions of Java that are vulnerable to CVE-2021-44228 with a default configuration. This playbook was created purely for research purposes and there's specific reason for running it other than if you'd like to see the results for yourself.
The infrastructure for this playbook consists of two cloud Trainman container tasks. The first task runs a web application that is vulnerable to the CVE-2021-44228 exploit and the second task runs the CVE-2021-44228 exploit against the first task. This operation is repeated over and over, with each subsequent run testing against a different version of Java. To accomplish this, the playbook instructs the first Trainman container task to start the vulnerable web application using a specific Java version. After the exploit is run and the results are recorded, the vulnerable web application is shutdown and restarted using a different Java version and then the exploit is executed again.
This playbook tests against Java versions that are available in Stanley Shyiko's Jabba Java version manager.
Requirements
None
Architecture
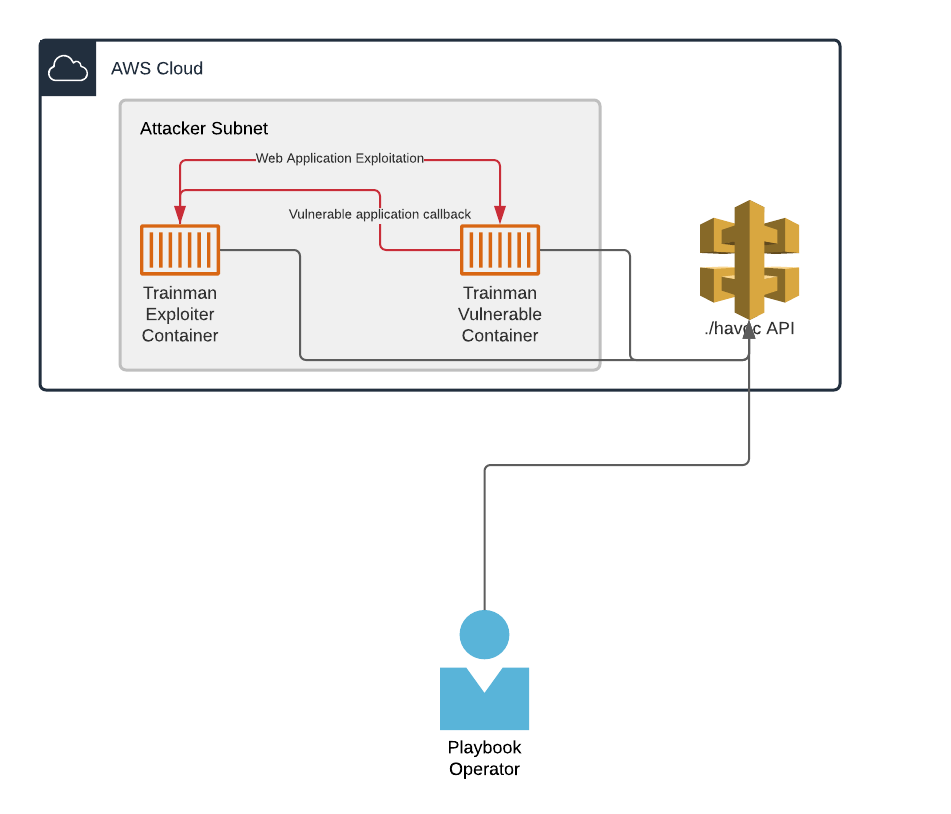
Configuration
To configure this playbook, use the ./havoc -c CLI option, select the number associated with the cve_2021_44228_testing playbook and provide the requested details:
$ ./havoc -c
1) c2_and_http_server 7) pse_recon_portscan
2) c2_with_ad_dc 8) pse_recon_reverse_dns
3) cve_2021_44228_exploit_and_c2 9) pse_recon_share_finder
4) cve_2021_44228_testing 10) simple_exfil
5) pse_lateral_movement_invoke_wmi 11) windows_exfil
6) pse_recon_bloodhound 12) windows_recon
Select a playbook to install: 4
Configuring playbook cve_2021_44228_testing.
If you have previously configured this playbook, configuring it again will delete the existing configuration.
Are you sure you want to continue? [Y/N]: y
Creating a customized cve_2021_44228_testing.ini file.
Provide a value for each parameter.
Press enter without providing a value to accept the default.
[general]
java_versions_to_test [<snip>]: <comma_separated_list_of_java_versions>
[cve_2021_44228_exploit_task]
http_port [80]: <http_port>
ldap_port [1389]: <ldap_port>
domain_name [None]: <domain_name|None>
exec_cmd [touch /opt/havoc/shared/$JAVA_VERSION]: <command_to_execute>
[cve_2021_44228_vulnerable_task]
http_port [80]: <http_port>
domain_name [None]: <domain_name|None>
<snip - installing required Python modules>
Playbook cve_2021_44228_testing configured.
$
Execution
To execute this playbook, run the following ./havoc CLI command (where is replaced with the ./havoc config profile name that you would like to authenticate to the ./havoc API with):
$ ./havoc -e cve_2021_44228_testing <profile>
Clean up
Error handling
If the playbook encounters errors during execution, it should automatically switch to a clean_up function and delete any resources that it created. If the playbook is hung on a specific task, you can press Ctrl+C to terminate the playbook and initiate the clean_up function.
Successful execution
After the playbook executes all operations successfully it will automatically initiate the playbook's clean_up function.
Associated resources
This playbook creates and destroys the following resources:
- A cloud Trainman container task that executes the log4shell exploit to act as the attacker.
- A cloud Trainman container task that runs the log4shell vulnerable web application to act as the victim.
- A portgroup that restricts inbound access to the attacking Trainman container task's HTTP and LDAP ports to just the public IP address of the victim Trainman container task that will be running the vulnerable web application.
- A portgroup that restricts inbound access to the victim Trainman container task's HTTP port to just the public IP address of the attacking Trainman container task that will be executing the log4shell exploit.
If you're uncertain whether the clean_up function completed successfully, the following ./havoc CLI console commands can be used to check which resources are still present:
list_tasks
list_portgroups
Updated over 2 years ago
