pse_lateral_movement
The pse_lateral_movement playbook utilizes an existing PowerShell Empire container task and connected C2 agent to perform various lateral movement activities. This playbook does not create the required PowerShell Empire container task or C2 agent components so they must be initialized by another playbook such as the c2_and_http_server playbook.
Requirements
Running this playbook requires the following pre-existing components:
- A PowerShell Empire container task with an established connection from a C2 agent.
Note that the PowerShell Empire task name and C2 agent name to be used by the playbook must be specified in the
task_nameandagent_nameparameters when configuring the playbook. - A second machine to move laterally to.
Architecture
The architecture and workflow of these playbooks look as follows:
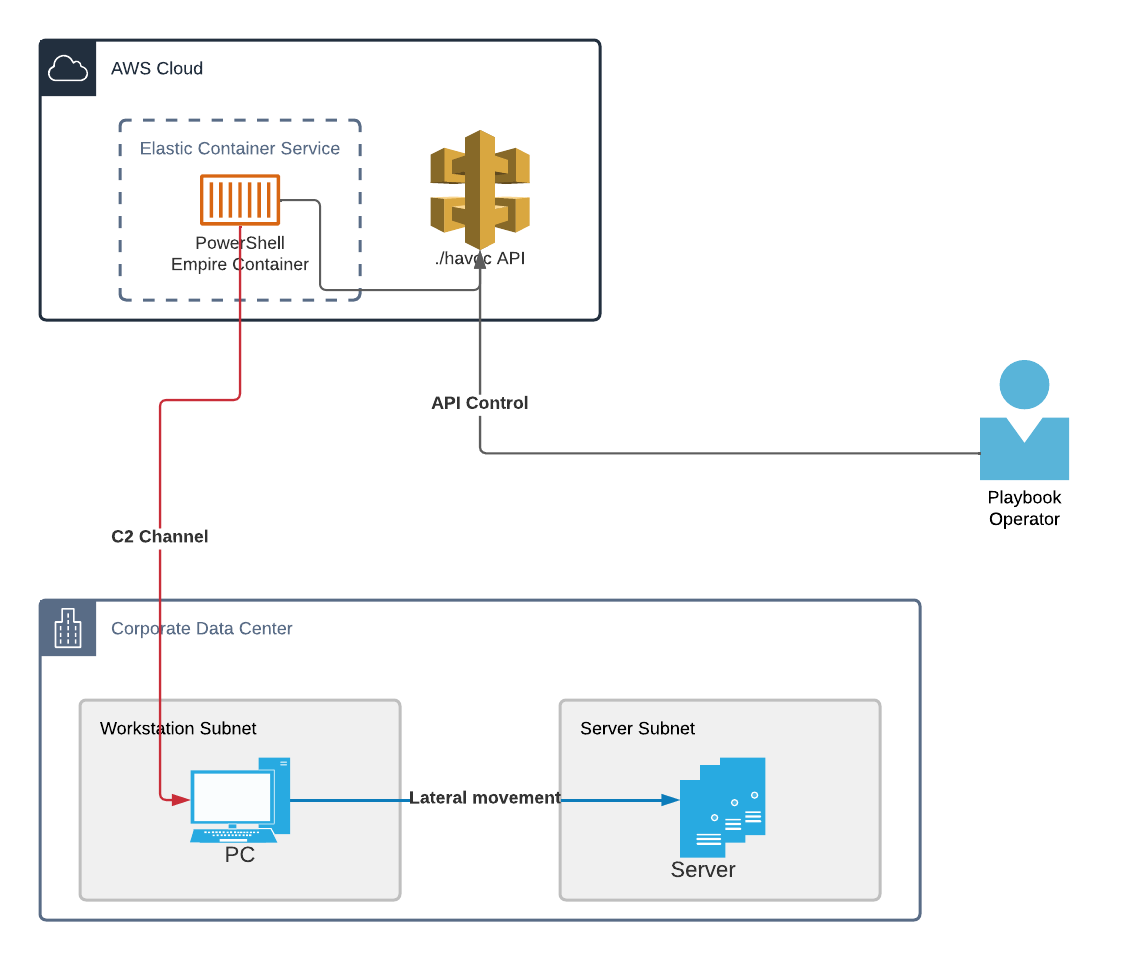
Configuration
To configure the pse_lateral_movement playbook, use the ./havoc -c CLI option, select the number associated with the pse_lateral_movement playbook and provide the requested details.
Required parameters:
[c2_task]
task_name - the task name assigned to the PowerShell Empire task.
agent_name - the name assigned to the agent that is connected to the PowerShell Empire task.
[module]
Enable - indicate if this module should be executed by the playbook (True|False).
Module - the powershell empire module to execute.
[invoke_wmi]
CredID - (optional) CredID from the store to use.
ComputerName - (required) host[s] to execute the stager on, comma separated.
Listener - (required if Command not specified) listener to use.
Command - (required if Listener not specified) custom command to run.
Obfuscate - (optional) obfuscate the launcher powershell code (True|False). Uses the ObfuscateCommand
for obfuscation types. For powershell only.
ObfuscateCommand - (optional) the Invoke-Obfuscation command to use. Only used if Obfuscate switch
is True. For powershell only.
Bypasses - (optional) bypasses as a space separated list to be prepended to the launcher.
UserName - (optional) [domain]username to use to execute command. Defaults to current user context.
Password - (optional) password to use to execute command.
UserAgent - (optional) user-agent string to use for the staging request (default|none|other).
Proxy - (optional) proxy to use for request (default|none|other).
ProxyCreds - (optional) proxy credentials to use for the request (default|none|other).
[invoke_psexec]
ComputerName - (required) host to execute the stager on.
ServiceName - (required) the name of the service to create.
Listener - (required if Command not specified) listener to use.
Command - (required if Listener not specified) custom command to run.
ResultFile - (optional) name of the file to write the results to on agent machine.
Obfuscate - (optional) obfuscate the launcher powershell code (True|False). Uses the ObfuscateCommand
for obfuscation types. For powershell only.
ObfuscateCommand - (optional) the Invoke-Obfuscation command to use. Only used if Obfuscate switch
is True. For powershell only.
Bypasses - (optional) bypasses as a space separated list to be prepended to the launcher.
UserAgent - (optional) user-agent string to use for the staging request (default|none|other).
Proxy - (optional) proxy to use for request (default|none|other).
ProxyCreds - (optional) proxy credentials to use for the request (default|none|other).
$ ./havoc -c
1) activity_report 3) pse_host_recon 5) pse_network_recon
2) c2_and_http_server 4) pse_lateral_movement 6) simple_exfil
Select a playbook to configure: 4
Configuring playbook pse_lateral_movement.
If you have previously configured this playbook, configuring it again will delete the existing configuration.
Are you sure you want to continue? [Y/N]: y
Creating a customized pse_lateral_movement.ini file.
Provide a value for each parameter.
Press enter without providing a value to accept the default.
[c2_task]
task_name [c2_server_mm_dd_YYYY_HH_MM]: <c2_task_name>
agent_name [1w2x3y4z]: <agent_name>
[invoke_wmi]
Enable [True]:
Module [powershell/lateral_movement/invoke_wmi]:
CredID []:
ComputerName []: <hostname_or_ip_address>
Listener []: <listener_name>
Command []:
Obfuscate []:
ObfuscateCommand []:
Bypasses []:
UserName []:
Password []:
UserAgent []:
Proxy []:
ProxyCreds []:
[invoke_psexec]
Enable [True]:
Module [powershell/lateral_movement/invoke_psexec]:
ComputerName []: <hostname_or_ip_address>
ServiceName []: <service_name>
Listener []: <listener_name>
Command []:
ResultFile []:
Obfuscate []:
ObfuscateCommand []:
Bypasses []:
UserAgent []:
Proxy []:
ProxyCreds []:
<snip - installing required Python modules>
Playbook pse_lateral_movement configured.
$
Execution
To execute the pse_lateral_movement playbook, run the following ./HAVOC CLI command (where <profile> is replaced with the ./HAVOC config profile name that you would like to authenticate to the ./HAVOC API with):
$ ./havoc -e pse_lateral_movement <profile>
Clean up
Error handling
If the playbook encounters errors during execution, it will self terminate. If the playbook is hung on a specific task, you can press Ctrl+C to terminate the playbook.
Successful execution
After the playbook executes all operations successfully it will self terminate.
Associated resources
This playbook does not create any resources.
Updated about 2 years ago
