pse_network_recon
The pse_network_recon playbook utilizes an existing PowerShell Empire container task and connected C2 agent to perform various network reconnaissance activities. This playbook does not create the required PowerShell Empire container task or C2 agent components so they must be initialized by another playbook such as the c2_and_http_server playbook.
Requirements
Running this playbook requires the following pre-existing components:
- A PowerShell Empire container task with an established connection from a C2 agent.
Note that the PowerShell Empire task name and C2 agent name to be used by the playbook must be specified in the
task_nameandagent_nameparameters when configuring the playbook.
Architecture
The architecture and workflow of this playbooks look as follows:
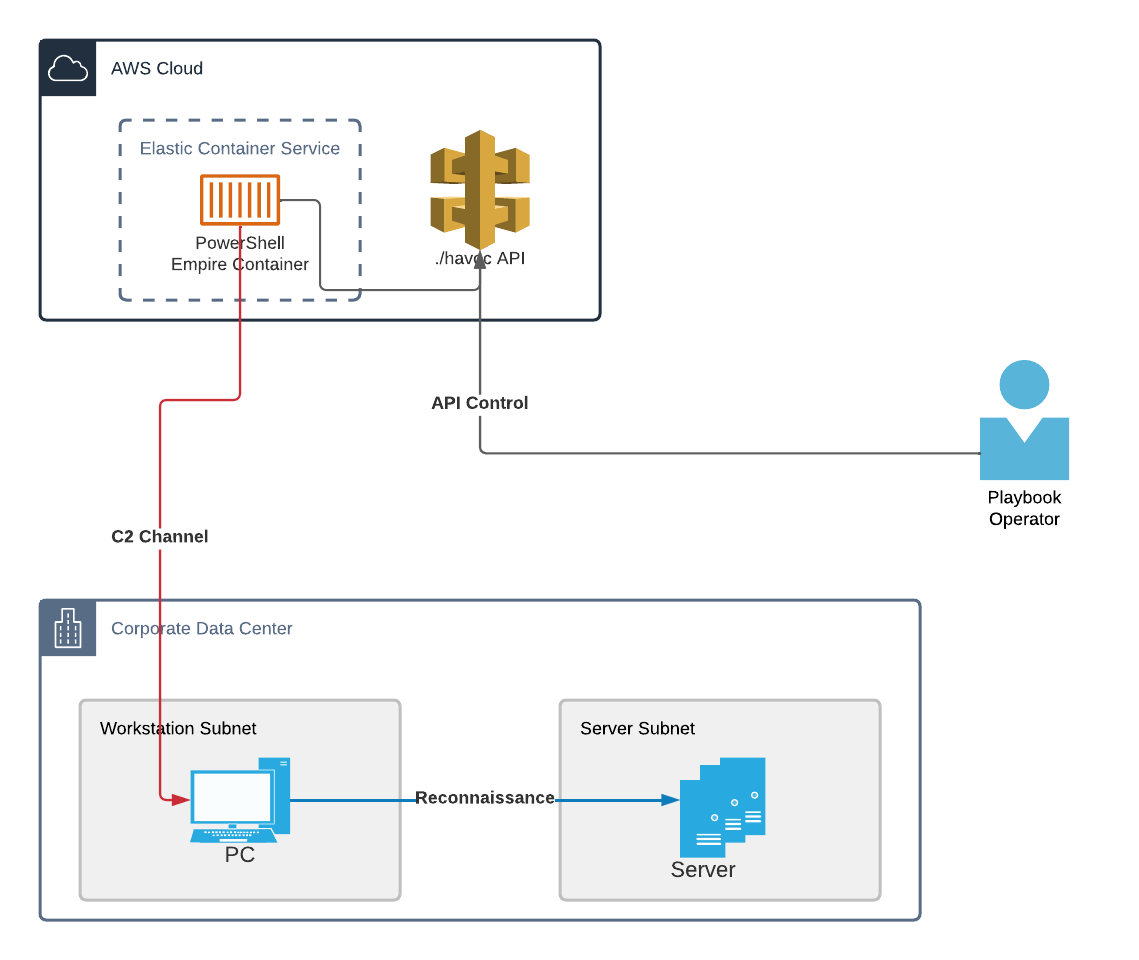
Configuration
To configure the pse_network_recon playbook, use the ./havoc -c CLI option, select the number associated with the pse_network_recon playbook and provide the requested details.
Required parameters:
[c2_task]
task_name - the task name assigned to the PowerShell Empire task.
agent_name - the name assigned to the agent that is connected to the PowerShell Empire task.
[module]
Enable - indicate if this module should be executed by the playbook (True/False).
Module - the powershell empire module to execute.
Optional parameters present for all modules:
completion_string - a string that should be present in the results to indicate the module is done. If not specified results are returned as soon as any results data becomes available, which may lead to incomplete results being returned.
Additional parameters per module:
[portscan]
AllformatsOut - (optional) output file of all formats.
ExcludeHosts - (optional) comma separated list of hosts to exclude.
GrepOut - (optional) greppable (.gnmap) output file.
HostFile - (required if Hosts not specified) input hosts from file (on the target).
Hosts- (required if HostFile not specified) hosts to scan. Can be a comma separated list of individual hosts or a CIDR range.
Open- (optional) only show hosts with open ports (True|False).
PingOnly- (optional) ping only, don't scan for ports (True|False).
Ports- (required) ports to scan for. Can be a comma separated list or a range.
ReadableOut- (optional) readable (.nmap) output file.
SkipDiscovery- (optional) treat all hosts as online (True|False).
TopPorts- (optional) scan for X number of top ports.
XmlOut- (optional) .XML output file.
[reverse_dns]
CIDR- (required if Range not specified) CIDR IP address block to perform reverse DNS on.
Range- (required if CIDR not specified) range of IP addresses to perform reverse DNS on.
[get_domain_controller]
Domain- (optional) the domain to query for domain controllers. Defaults to the current domain.
Server- (optional) specifies an Active Directory server (domain controller) to bind to.
LDAP- (optional) use LDAP queries to determine the domain controllers (True|False).
[get_domain_policy]
Policy- (required) extract Domain or DC (domain controller) policies, or All.
Domain- (optional) the domain to query for default policies. Defaults to the current domain.
Server- (optional) specifies an Active Directory server (domain controller) to bind to.
ServerTimeLimit- (optional) specifies the maximum amount of time the server spends searching. Default is 120 seconds.
[bloodhound]
CollectionMethod- (required) the method to collect data. 'Group', 'ComputerOnly', 'LocalGroup',
'GPOLocalGroup', 'Session', 'LoggedOn', 'Trusts, 'Stealth', or 'Default'.
Threads- (required) the maximum concurrent threads to execute.
Throttle- (optional) the number of cypher queries to queue up for neo4j RESTful API ingestion.
CSVFolder- (optional) the CSV folder to use for output. Defaults to the current folder location.
CSVPrefix- (optional) A prefix for all CSV files.
ComputerADSpath- (optional) the LDAP source to search through for computers, e.g. "LDAP://OU=secret,DC=testlab,DC=local".
ComputerName- (optional) array of one or more computers to enumerate.
Domain- (optional) the domain to use for the query. Defaults to the current domain.
DomainController- (optional) domain controller to reflect LDAP queries through.
GlobalCatalog- (optional) the global catalog location to resolve user memberships from.
SearchForest- (optional) search all domains in the forest (True|False).
SkipGCDeconfliction- (optional) skip global catalog enumeration for session deconfliction (True|False).
URI- (optional) the BloodHound neo4j URL location (http://host:port/).
UserADSPath- (optional) the LDAP source to search through for users/groups, e.g. "LDAP://OU=secret,DC=testlab,DC=local".
UserPass- (optional) the "user:password" for the BloodHound neo4j instance.
$ ./havoc -c
1) activity_report 3) pse_host_recon 5) pse_network_recon
2) c2_and_http_server 4) pse_lateral_movement 6) simple_exfil
Select a playbook to configure: 5
Configuring playbook pse_network_recon.
If you have previously configured this playbook, configuring it again will delete the existing configuration.
Are you sure you want to continue? [Y/N]: y
Creating a customized pse_network_recon.ini file.
Provide a value for each parameter.
Press enter without providing a value to accept the default.
[c2_task]
task_name [c2-http_mm_dd_YYYY_HH_MM]: <c2_task_name>
agent_name [1w2x3y4z]: <agent_name>
[portscan]
Enable [True]: <True|False>
Module [powershell/situational_awareness/network/portscan]: <module_path>
AllformatsOut []: <file_name>
ExcludeHosts []: <hosts_to_exclude>
GrepOut []: <file_name>
HostFile []: <file_name>
Hosts []: <ip_addresses>
Open []: <True|False>
PingOnly []: <True|False>
Ports [1-1024]: <port_numbers>
ReadableOut []: <file_name>
SkipDiscovery []: <True|False>
TopPorts []: <count>
XmlOut []: <file_name>
completion_string [completed]: <completion_string>
[reverse_dns]
Enable [True]: <True|False>
Module [powershell/situational_awareness/network/reverse_dns]: <module_path>
CIDR []: <cidr_block>
Range []: <ip_range>
completion_string [completed]: <completion_string>
[get_domain_controller]
Enable [True]: <True|False>
Module [powershell/situational_awareness/network/powerview/get_domain_controller]: <module_path>
Domain []: <domain>
Server []: <ad_server>
LDAP []: <True|False>
completion_string [completed]: <completion_string>
[get_domain_policy]
Enable [True]: <True|False>
Module [powershell/situational_awareness/network/powerview/get_domain_policy]: <module_path>
Policy [Domain]: <Domain|DC|All>
Domain []: <domain>
Server []: <ad_server>
ServerTimeLimit []: <seconds>
completion_string [completed]: <completion_string>
[bloodhound]
Enable [True]: <True|False>
Module [powershell/situational_awareness/network/bloodhound]: <module_path>
CollectionMethod [Default]: <Group|ComputerOnly|LocalGroup|GPOLocalGroup|Session|LoggedOn|Trusts|Stealth|Default>
Threads [20]: <max_threads>
Throttle [1000]: <max_bloodhound_queries>
CSVFolder []: <file_output_path>
CSVPrefix []: <file_name_prefix>
ComputerADSpath []: <ldap_source>
ComputerName []: <array_of_hostnames>
Domain []: <domain>
DomainController []: <hostname_or_ip_address>
GlobalCatalog []: <global_catalog_location>
SearchForest []: <True|False>
SkipGCDeconfliction []: <True|False>
URI []: <bloodhound_server_uri>
UserADSPath []: <ldap_source>
UserPass []: <bloodhound_user:bloodhound_password>
completion_string [completed]: <completion_string>
<snip - installing required Python modules>
Playbook pse_network_recon configured.
$
Execution
To execute a pse_recon playbook, run the following ./havoc CLI command (where <profile> is replaced with the ./havoc config profile name that you would like to authenticate to the ./havoc API with) and the playbook name reflects the specific pse_recon playbook you would like to execute:
$ ./havoc -e pse_network_recon <profile>
Clean up
Error handling
If the playbook encounters errors during execution, it will self terminate. If the playbook is hung on a specific task, you can press Ctrl+C to terminate the playbook.
Successful execution
After the playbook executes all operations successfully it will self terminate.
Associated resources
These playbooks do not create any resources.
Updated about 2 years ago
